What Is DarkSide Ransomware?
Initially traced back to a Russian speaking cybercriminal, DarkSide was announced as a Ransomeware-as-a-Service. “Affiliates” are recruited to launch attacks using this Ransomware toolset.
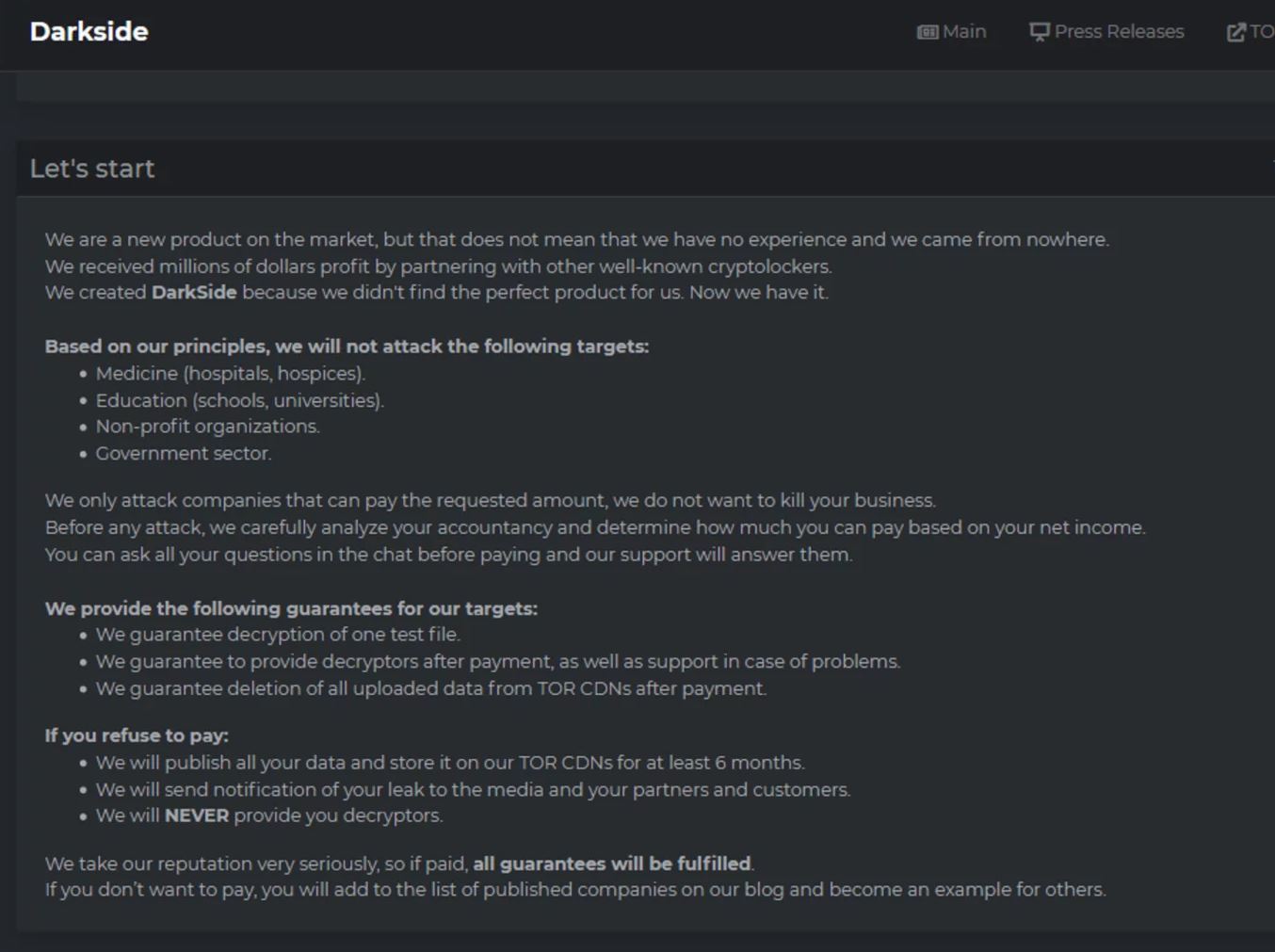
DarkSide affiliates seem to follow a code of conduct where they have to agree NOT to target hospitals, schools, nonprofits or government organisations.
Instead, they take a focused approach targeting large commercial businesses whom they believe can pay a ransom.
(Initial accouncement of DarkSide - credit areteir.com)
What Tactics Does a DarkSide Ransomware Attack Use?
DarkSide typical ransom requests exceed $5million, and like most complex attacks, it is multi-faceted and well planned.
A DarkSide attack will start with “reconnaissance” using penetration tools to gain initial access to your systems.
After successfully getting initial access, DarkSide attackers will spend as long as two weeks hunting for vulnerabilities and gaining access to privileged user accounts.
They will do this to maximise the impact when they eventually lock your systems.
The attack will download data from your systems, which the attackers will threaten to make public if a ransom isn’t paid. DarkSide will then lock or delete that data creating a .txt file detailing every system and file they have breached. This .txt file is made visible to victims once the DarkSide payload activates.
How Do You Defend Against DarkSide?
DarkSide is a multi-vector attack that exploits email as an entry point, endpoints as a way to infect and traverse your networks and skilled operators that navigate your systems. Robust email, endpoint, network monitoring and authentication protection are all required to minimise the chance of this attack.
DarkSide favours Windows vulnerabilities. So as is the case with all security advice, it remains vital to keep your windows systems updated.